SSO and Directory Sync with Precisely
Learn more about Precisely's SSO login integration and a way to manage your users and teams by synchronizing your Directory
Maximize Precisely’s integration with your general workspace!
Our team can link your Precisely account to your existing workspace. We currently offer Single Sign-on integration and synchronization with your directory that can make your workflows even more efficient.
Single Sign-On (SSO)
With the Single Sign-on (SSO) integration, you and your coworkers can easily access the Precisely platform using the same authentication method - such as Microsoft Entra ID, Okta, Google and OneLogin - as with all your work-related apps. By doing this, account management becomes easier and security greater as no user needs to remember passwords. Contact us to get SSO enabled for your organization in Precisely.
Directory Sync
If your company uses one directory - such as Microsoft Entra ID or Okta - to keep a track of the employees and the given access to different work tools, Precisely can also be synchronized via directory.
With directory sync, you are able to keep full control of your employees that are also Precisely users. This is possible even if your company has multiple organizations within Precisely.

For technical reasons, it is required to also have the SSO integration in order to synchronize your directory with Precisely. Note that you do not necessarily need to use the same provider for SSO and AD. Contact us to get AD and SSO enabled for your organization in Precisely.
How to: Adding users to Precisely via directory
To be able to provision users through your directory, you'll first need to configure the connection according to the instruction given by the Precisely Team (see how to contact us). This is usually done by the IT team.
Then, you'll be able to start creating groups and adding users. There are several ways of provisioning and managing users in Precisely from your directory.
- 1. Provisioning users only (no user role specified)
- 2. Provisioning users according to their user role
- 3. Managing users and their team membership
⚠️ For a user to be successfully provisioned (added) to Precisely through directory, you must choose either Option 1 or Option 2.
Option 3 (organizing teams) is not mandatory, and it can only be used after users have been provisioned (added) to Precisely through Option 2 (according to their user role).
👇 Keep reading for detailed instructions on each option.
1. Provisioning users only (no user role specified)
To provision users without specifying their user role (admin/manager/member/viewer), you only need to create one group per organization in your directory with the following naming convention:
Precisely/<org_id>
Reference <org_id> needs to be replaced by your Precisely organization ID, which can be found in the top right bar by clicking the organization's name.
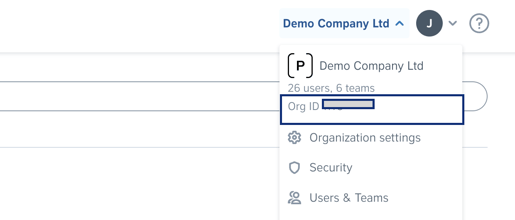
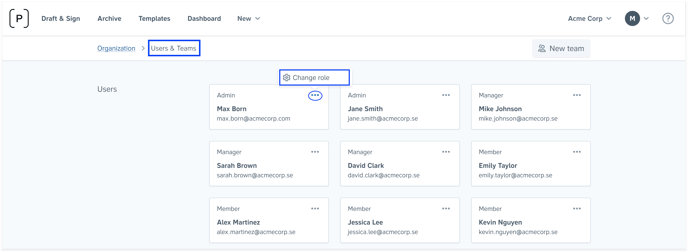
All users in Precisely will automatically get member user roles. The roles need to be manually adjusted directly in the Precisely platform in the Users & Teams settings. Please note that only admin users are able to access these settings.
2. Provisioning users according to their user role
You're also able to directly provision users together with their user role (admin/manager/member/viewer).
In that case, you need to create 4 different groups following the naming convention below.
Precisely/<org_id>/Adminsthe user is added to the Precisely organization as an admin
Precisely/<org_id>/Managersthe user is added to the Precisely organization as a manager
Precisely/<org_id>/Membersthe user is added to the Precisely organization as a member
Precisely/<org_id>/Viewersthe user is added to the Precisely organization as a viewer
Reference <org_id> needs to be replaced by your Precisely organization ID, which can be found in the top right bar by clicking the organization's name.

- Each user must be added to one of the groups above.
- Each user can be added to only one of the groups.
3. Managing users and their team membership
You're also able to set up a Precisely team membership for each user directly in your directory. This can only be done if you've previously provisioned a user according to their user role.
Teams in Precisely are departments or groups of team members in your organization (e.g. Legal, Accounting, Sales, Management, People & Culture, etc.). When you want to give that department or group access to a template, a folder, or a document, you share it with the team.
To organize users into their team already in your AD, use the following naming convention:
Precisely/<org_id>/Team/<team_name>
Reference <org_id> needs to be replaced by your Precisely organization ID, which can be found in the top right bar by clicking the organization's name.

Reference <team_name> should be replaced by the name of the specific team in the Precisely platform. Admin users are able to create teams in the Precisely platform under Users & Teams settings.
⚠️ Important!
- Make sure to write team names in the exact letters, since the names are case-sensitive (copy-paste is your best friend! 🤓)
- If you type in a team name in your AD that does not exist in the Precisely platform, that team will be automatically created in Precisely 🧠
- Team membership is optional. This means that one user can belong to several teams, or they don't have to belong to any team.
- Note that once you are provisioning users via directory/SSO, it is not possible to invite users or delete them directly from the platform. Adding and removing users will only be possible via directory.
Removing users from Precisely via directory
To deprovision (remove) a user from Precisely, they should be removed from the groups in your directory.
Please note that it is not enough to disable the account of a user in your system. The user should be specifically removed from directory groups belonging to Precisely.
Any questions remaining? Get in touch!